How ransomware variants are neutralizing data backups
The latest iterations of ransomware aim to undercut backups as an effective method for recovering from attacks. Learn how to overcome this vulnerability.
(Author: Brien Posey – originally published with TechTarget)
Ransomware, the monetization of malware, has been one of the most pervasive threats against business data for the last several years. Now a megabillion-dollar industry, ransomware variants are usually delivered by email attachments that allow attackers to encrypt a company’s data and hold the key to unlock the data for an exorbitant price.
The media has run story after story about businesses that have suffered massive financial losses following a ransomware attack. Some of the more recent victims include the Georgia Department of Agriculture, Mecklenburg County North Carolina and the Hackensack Sleep and Pulmonary Center in New Jersey.
Once an organization falls victim to a ransomware attack, it has two choices: pay the ransom or restore a backup. Three-quarters of IT decision-makers whose organizations haven’t been hit by ransomware said they wouldn’t pay a ransom, according to a survey conducted by cybersecurity vendor Trend Micro. When faced with the reality of an attack, however, nearly two-thirds (65%) of previously infected companies surveyed paid up.
The FBI advises against paying the ransom because doing so doesn’t guarantee your data will be returned. There are documented instances of companies paying a ransom and never receiving decryption keys or then being told they need to pay more. Ultimately, paying a ransom emboldens the perpetrators.
This leaves backup restoration as the best option for coping with a ransomware attack. But even this option isn’t foolproof.
Inadequate restorations
For one thing, some companies discover their backups are inadequate. For example, they may have omitted certain systems or data from their backups either accidentally or to reduce costs. Likewise, some organizations fail to test their backups, discovering only after an attack that the backups can’t be restored.
These types of problems are preventable if you take time to review and test backups before disaster strikes. Far more troubling is how ransomware is becoming more pervasive, and new ransomware variants are increasingly more sophisticated. Some victims have found ransomware not only encrypts data, but also destroys backups.
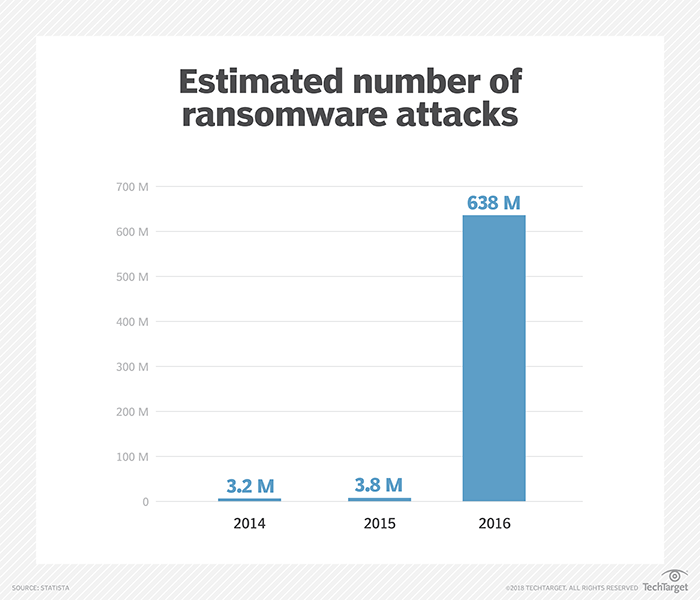
New ransomware variants target backups
The degree to which ransomware can harm backups varies according to a number of factors, including the ransomware variant involved and the way in which the data is protected. Most modern backup products for Windows use shadow copies and system restore points. But several types of ransomware, such as Locky and Crypto, are known to destroy shadow copies and restore point data.
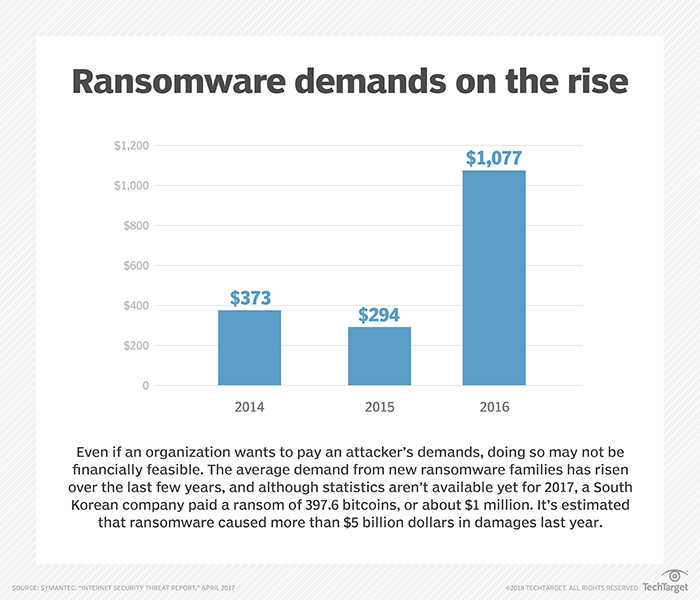
Replication’s hidden danger
Smaller businesses or branch offices of larger organizations sometimes use replication to protect data. Hypervisor vendors such as VMware and Microsoft, for example, offer native replication features that allow a standby host to replicate. If something happened to the primary copy of a virtual machine (VM), then the replica can be activated and brought online. Of course there are other types of replication that are sometimes used for data protection. Many storage vendors provide storage array-level replication features as a tool for protecting against data loss.
Replication works as a contingency for hardware failure and, on its own, does almost nothing to protect against ransomware. A replication engine can’t distinguish between malicious file encryption and a legitimate file modification. Hence, when ransomware encrypts a file, the malicious action is repeated on the replica, meaning the replica’s data also will be encrypted.
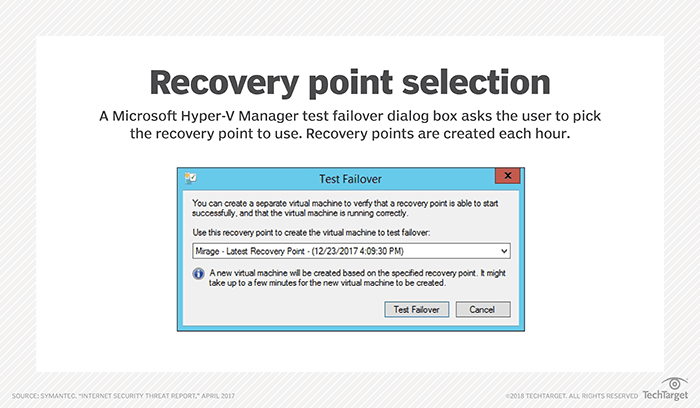
If your organization uses replication as a data protection mechanism, check to see if the replication engine allows for the creation of multiple recovery points. You can configure some replication products to retain a number of recovery points, so if the replica has to be activated, it can be reverted to a previous state. Microsoft’s Hyper-V, for example, allows for the creation of hourly recovery points. Hence, if a ransomware infection were to spread to a replica VM, then a failover could be performed using a replica recovery point created just prior to the ransomware attack, as shown in “Recovery point selection.”
The importance of an air gap
Revisit your permissions model
Ransomware infections often originate at network endpoints through the actions of careless, or unlucky, users. One of the best things you can do to minimize damage is to ensure users have only the permissions necessary for them to do their jobs and nothing more.
If a backup agent runs directly on a user’s PC, then it’s best to configure the backup agent to use a dedicated service account rather than simply piggybacking off of the end user’s account. This approach makes it possible to back up the system without giving the user backup permissions. If the user suffers a ransomware attack, then the ransomware will most likely use the end user’s security context, meaning its access will be limited to what the user has access to. Isolating the backups through using a service account may help to shield the backup process.
Best practices for ransomware prevention
Ransomware statistics are staggering. Simply put, there’s a high probability of any organization being attacked. Perhaps the scariest fact about ransomware is that attacks can happen repeatedly. Imagine the frustration of paying a ransom to get your data back, only to be hit by another attack an hour later. This has happened, and the attackers have no sympathy or mercy for their victims.
Given the seriousness of these attacks, organizations must take the threat seriously and take steps to prevent attacks. A backup should be the last line of defense against ransomware, not the first.
In the past, organizations have relied heavily on user education for malware prevention: If users can be taught to recognize a phishing email, then there’s little chance they’ll click on a malicious link in such a message. Unfortunately, experience has shown that even the best user education won’t completely mitigate the risk of users clicking on malicious links or opening malicious attachments.
A better approach is to assume that user education is ineffective. And a better strategy is to screen messages at the mail server level so phishing messages never make it to users’ mailboxes. Similarly, restrict user permissions in a way that minimizes damage should a ransomware attack occur.
There are a lot of ways of doing this. One particularly effective approach is to use application whitelisting so that users can’t run unauthorized processes. A more common approach is to perform a permissions audit and ensure that users only have write permissions where absolutely necessary. This won’t stop a ransomware infection from occurring, but because ransomware piggybacks on the user’s privileges, it won’t be able to touch anything the user doesn’t have access to. Hence, this approach limits the damage. Another option is to require the IT staff to use nonadministrative accounts unless they’re performing an action that specifically requires administrative privileges.
It’s important to remember phishing email messages are only one source of ransomware. It’s also common for attackers to use phony tech support scams as a means of introducing ransomware onto victim computers. Train end users to recognize the difference between a real phone call from IT and a scam. That’s easier said than done, however.
Ransomware protection bottom line
When it comes to protecting against ransomware, it is best to think of the problem as business continuity. Even if an organization is able to recover from a ransomware attack by restoring backups, the recovery process will take time to complete. As such, organizations shouldn’t focus solely on protecting backups against ransomware; they should also consider how to minimize the disruption caused by a ransomware attack.
When it comes to protecting against ransomware, it is best to think of the problem as business continuity. Even if an organization is able to recover from a ransomware attack by restoring backups, the recovery process will take time to complete. As such, organizations shouldn’t focus solely on protecting backups against ransomware; they should also consider how to minimize the disruption caused by a ransomware attack.
(Author: Brien Posey – originally published with TechTarget)

About the Author: Alex von Hassler’s long term focus is the continued testing, learning, and deployment of modern IT solutions. During his years as a DataSpan team member, his responsibilities grew from managing Salesforce CRM to improving system security, creating marketing initiatives, as well as providing continued support to the highly motivated and experienced team in an ever-changing industry. As DataSpan evolves to provide the best-fitting IT solutions to its customers, Alex von Hassler continues to hone his skills in the world of web-based ERP systems, security, and best customer engagement practices. Empowering such a dynamic team with the right tools provides him with enormous gratification.







